Export NSX DFW Rules using vRO
Many organisations are seeing the value of NSX-v in SDDC environments, however there is no easy way to export the NSX Distributed Firewall (DFW) rules from NSX to a CSV file. To export all rules in the environment, we need to extract each of the firewall rule IDs and get the details extracted for each rule. We will then export this information in a CSV file and optionally email it to the requestor.
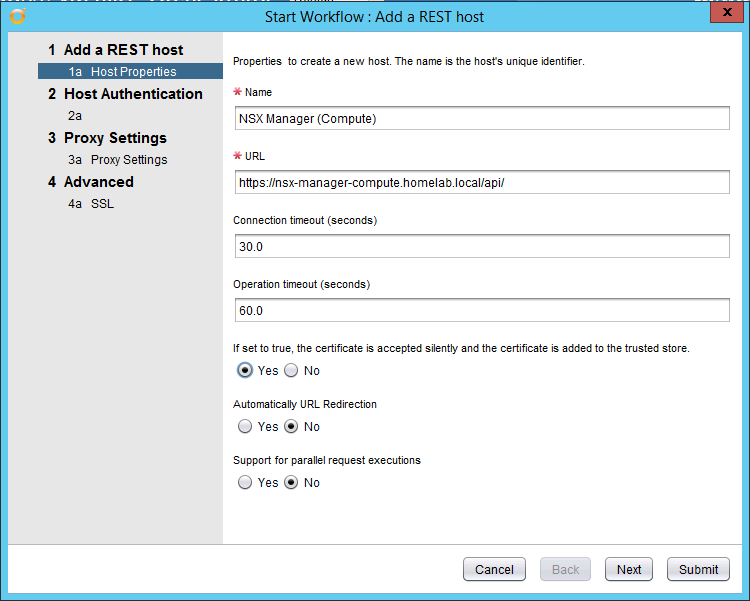
To begin, open vRO and create a HTTP-REST Host for each of your NSX Manager instances. Note the URL should be the FQDN with /api/ appended to the end.
Name: NSX Manager (Compute)
URL: https://nsx-manager-compute.homelab.local**/api/**
Silently accept the certificate: Yes
Host Authentication Type: Basic
Session Mode: Shared Session
Username: admin
Password: ****************
Once the REST Hosts have been added for each NSX Manager instance, import the workflow package com.gazflynn.nsx.export from GitHub or code.vmware.com to vRO and the workflows will be imported.
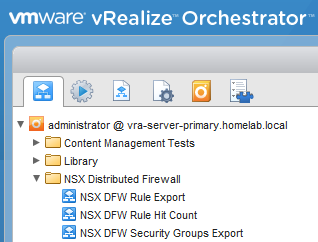
The vRO package contains three different workflows.
- NSX DFW Rule Export - This workflow will export a list of all Firewall Rules.
- NSX DFW Rule Hit Count - This workflow will export a list of all firewall rules with the hit count for each rule.
- NSX DFW Security Groups Export - This workflow will export a list of IP Addresses defined in each Security Group.
Before running each workflow, edit the workflow and adjust the email_xxxxxx attributes to suit your environment. You will need to enter a email_smtpHost, email_fromAddress etc. Once the attributes are set, run the workflow you wish. You are prompted to select if you want to email the CSV and if so, enter the recipients email addresses, and then select Submit. This will run the workflow and email the CSV file to the email addresses provided if selected. If you selected no to emailing the CSV file, it can be accessed from the vRO Server at the location /var/lib/vco/app-server/temp/<<filename>>.csv
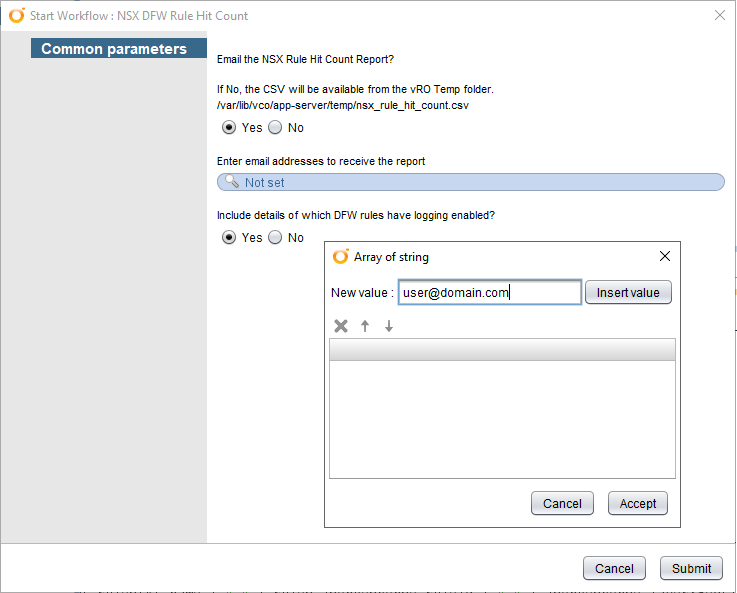
Once you have the CSV results, you can also use the workflow "NSX DFW Security Groups Export" to map the IPs listed in each Security Group referenced in the DFW rules.
Any suggestions on how to improve this or have a feature request? Please create an Issue on GitHub.
The output report will look like the sample below.